New Product: BLAST - Business Logic Application Security Testing
August 27, 2024
At Corgea, our mission has always been to empower developers and security teams with the tools they need to build and maintain secure applications. Today, we're excited to announce a new product that will change the way you think about application security testing: BLAST (Business Logic Application Security Testing).
What is BLAST?
BLAST represents the next generation of code scanning technology. While traditional Static Application Security Testing (SAST) has been the industry standard for years, it is not without its shortcomings. SAST tools rely on outdated methods, using simple keyword and pattern-based detection to identify vulnerabilities. This approach often leads to a high rate of false positives, no ability to reason, and an inability to understand the context of the code. Additionally, it's up to security and engineering teams to write and curate rules, which in many cases can't be written for these classes of vulnerabilities.
BLAST changes the game by integrating advanced Large Language Models (LLMs) with static analysis. This powerful combination gives BLAST the ability to reason like a human, understand the context of the code it scans, and accurately identify business logic vulnerabilities that SAST tools simply miss. With fewer false positives, developers can trust the results BLAST provides, enabling them to focus on fixing real issues instead of sifting through noise. And unlike traditional tools that can’t explain their findings, BLAST offers clear, understandable explanations that enhance your team’s understanding of potential risks.
Why BLAST Matters?
Every pull request (PR) is an opportunity to improve your application’s security, but PR reviews often miss critical issues due to time constraints and the limitations of existing tools. BLAST ensures that every PR gets a thorough security review, uncovering vulnerabilities that were previously undetectable and providing actionable insights that reduce the burden on your developers. By catching issues early, BLAST helps you prevent security incidents before they occur, reducing the risk of breaches and the associated costs.
BLAST doesn’t just improve security—it makes the entire development process more efficient. With fewer false positives and clearer, more actionable findings, your team spends less time triaging alerts and more time building features. Plus, by integrating seamlessly with your existing workflows, BLAST provides this added security without adding friction to your process.
What can BLAST detect?
BLAST can detect many classes of vulnerabilities that have been extremely hard to find. We're starting with the following list of CWEs that AppSec leaders have been asking about:
Business Logic Vulnerabilities (CWE-840): These are flaws in the app’s design that let users do things they shouldn't, like bypassing purchase limits or manipulating transactions.
Code Logic Vulnerabilities (CWE-633): Errors in the code’s logic, such as incorrect conditions or loops, can cause the program to behave unexpectedly.
Insecure Authentication (CWE-287): This happens when multi-factor authentication is missing, or authentication tokens are not handled securely.
Insecure Authorization (CWE-285): This allows users to access resources or perform actions they shouldn't, due to weak access controls.
Context Dependent Vulnerabilities (CWE-696): These vulnerabilities only occur under certain conditions, like time-based or state-dependent errors.
Improper Session Management (CWE-384): Weak handling of session identifiers, such as predictable session IDs, insecure transmission, or storage, can lead to session hijacking or unauthorized access.
Timing Attacks (CWE-208): Attackers exploit the time taken to execute operations, like encryption, to gain sensitive information.
Race Conditions (CWE-362): Flaws that occur when the result depends on the order or timing of events that can't be controlled, leading to insecure outcomes.
Unhygienic Data Handling (CWE-20): Poor handling of data, like not escaping special characters, can lead to vulnerabilities.
Insecure Data Storage (CWE-311): Sensitive data is stored insecurely, such as in plaintext or with weak encryption.
Sensitive Data Exposure (CWE-200): Sensitive information is unintentionally revealed, such as through logs or error messages.
Improper Session Management (CWE-384): Weak handling of session identifiers, like predictable session IDs, can lead to security risks.
Improper Error Handling (CWE-209): Errors are not managed securely, potentially leaking information or causing unintended behavior.
Improper Logging (CWE-532): Sensitive data is logged, or important security events are not logged, leading to risks.
Improper Exception Handling (CWE-248): Poor management of exceptions can cause crashes, data loss, or exposure of sensitive information.
We will continue on this list based on results and customer feedback.
Real-World Examples
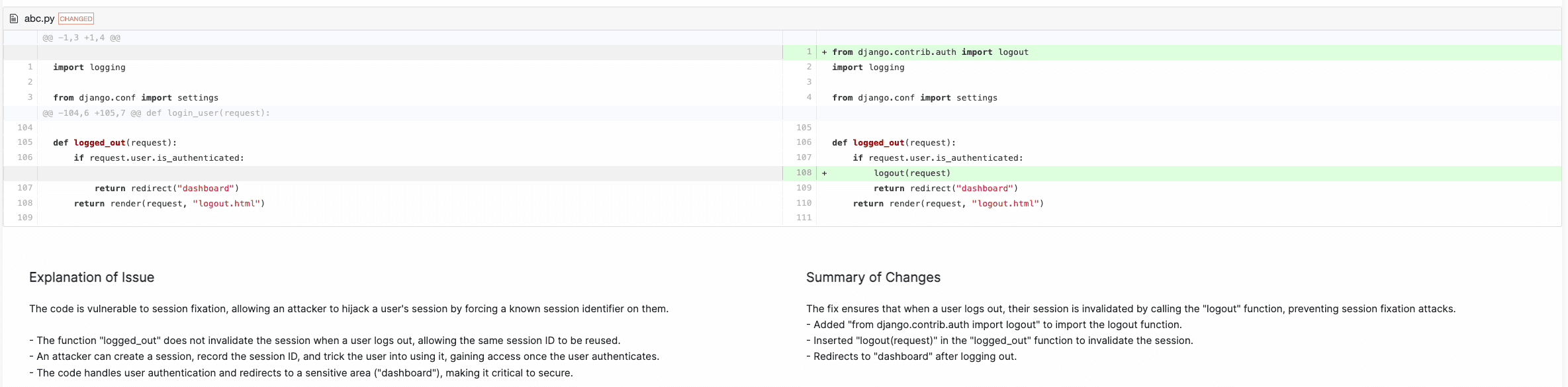
BLAST has already proven its value in real-world scenarios. For instance, in one case, BLAST identified a critical issue with improper session management (CWE-384) in a Django application—a vulnerability that could have easily gone unnoticed with traditional SAST tools or human reviewers. This example highlights how very simple code could lead to a very serious vulnerability.
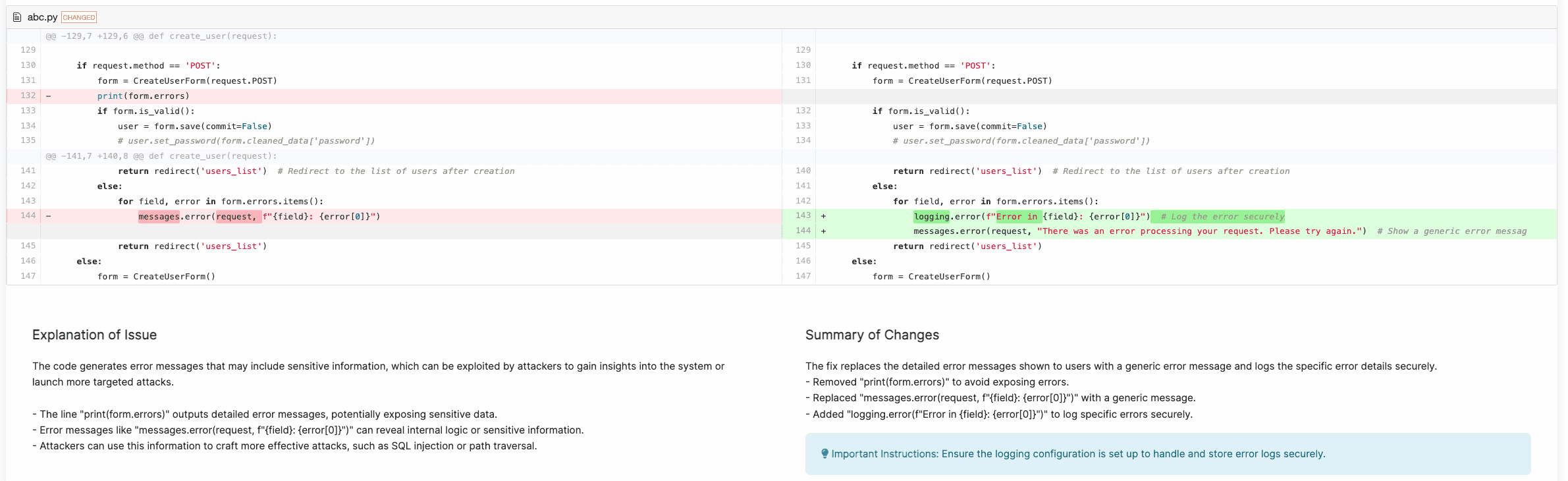
Another example that requires context to detect is the following Generation of Error Message Containing Sensitive Information vulnerability (CWE-209). The code generates error messages that may include sensitive information, which can be exploited by attackers to gain insights into the system or launch more targeted attacks. Corgea is able to understand the context that this pertains to user data, and that rendering error messages from a user can expose system information.
Conclusion
The launch of BLAST marks a significant milestone in our journey to redefine application security. By combining the best of LLM and static analysis technology, BLAST provides a smarter, more reliable way to detect and mitigate business logic vulnerabilities. We believe that with BLAST, your applications will not only be more secure but also developed more efficiently.
Sign up to the Corgea BLAST Beta waitlist or setup a demo to learn how Corgea finds, triages and fixes logic vulnerabilities.
Ready to fix with a click?
Harden your software in less than 10 mins'